TERMS OF USE
I have read and understand the Conflux Grants Ecosystem Overview, and determined that my proposal is best for the Technical Grants stream (YES).
I understand that the Conflux Technical Grants are subject to a No Sale Rule, and I have read the terms of this rule (YES).
I understand that I will be required to provide additional KYC information to the Conflux Foundation to receive this grant (YES).
I understand that I will be required to follow public grant reporting requirements (YES).
APPLICATION INTRODUCTION
Project: MetaScout
MetaScout is a highly regarded real-time smart contract security monitoring tool widely used in the cryptocurrency space.
Are you an incorporated startup?
MetaTrust Labs
Links to the project’s webpage, DApp, project social handles, and chat groups.
Website: metatrust.io
Twitter: https://twitter.com/MetaTrustLabs
Telegram: https://t.me/metatrustlabs
Linkedin: https://www.linkedin.com/in/metatrust
What is your Conflux eSpace recipient wallet address for the grant?
0x3Dc4e40F0db36933A400Ba14E64Dad46Caa53d64
TECHNICAL INTRODUCTION
 About MetaScout
About MetaScout
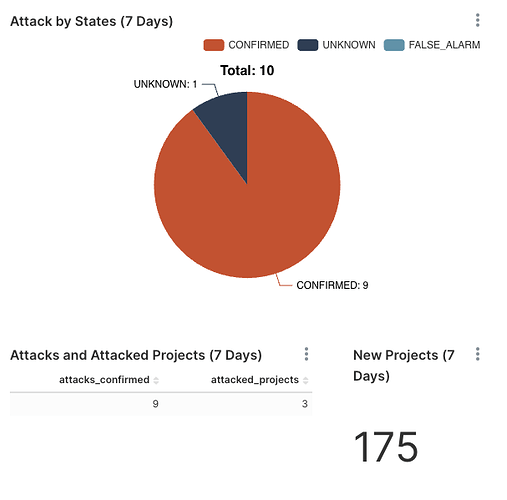
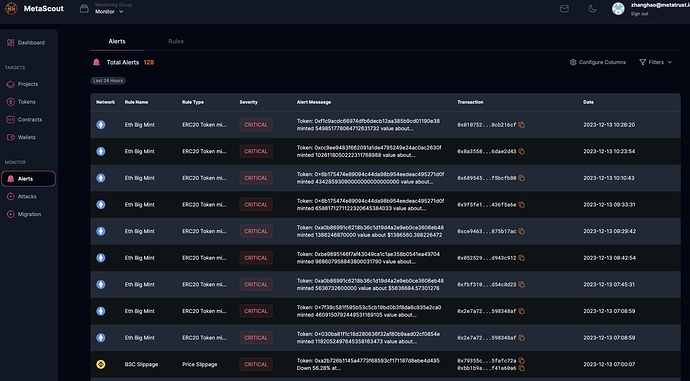
MetaScout is a highly regarded real-time smart contract security monitoring tool widely used in the cryptocurrency space.MetaScout offers a number of benefits including 24/7 on-chain security monitoring and real-time anomalous behavior tracking, which helps projects protect against suspicious attacks and proactively identify and address smart contract vulnerabilities to mitigate potential financial risks. In addition to monitoring, MetaScout also provides “Migration Attack” security services, acting as a security superhero in the event of an attack.
In the event of an attack, it scans the blockchain for similar smart contracts and sends out alerts about contracts that are vulnerable to the same attack. It uses multiple engines, such as code snippet analysis and CFG similarity, to achieve an impressive hit rate of over 90%.
 MetaScout Core Features
MetaScout Core Features
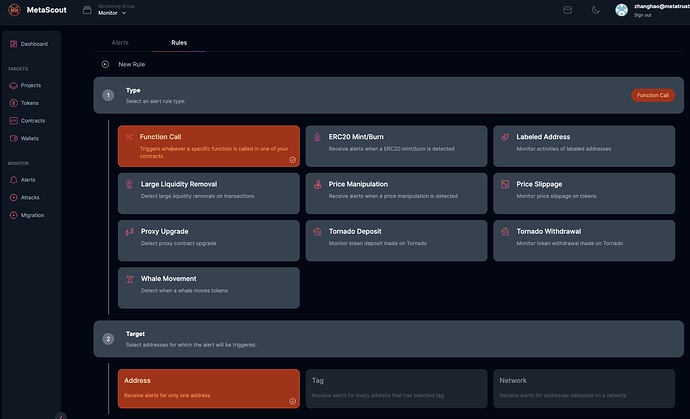
- Mempool Monitoring: Implements advanced mempool monitoring for early threat detection.
- Migration Attack Detection: Utilizes bytecode, function, and snippet similarity engines to enhance security.
- Smart Contract Firewall: Offers on-chain protection through proxy firewall, forwarder callback, and ERC4771 Lib contracts.
- Early-Response System: Swiftly responds to critical events like mempool attacks with an early-stop mechanism.
 What MetaScout can do on Conflux?
What MetaScout can do on Conflux?
- Enhanced Security Infrastructure: MetaScout addresses security vulnerabilities on the Conflux network by implementing advanced features such as proactive monitoring, threat detection, and rapid incident response. This fortification helps create a more secure environment for users and developers, mitigating potential risks.
- Real-Time Monitoring and Incident Response: MetaScout introduces a robust monitoring infrastructure tailored for Conflux, enabling real-time tracking of activities. This includes efficient incident response mechanisms to swiftly identify and address security incidents, reducing the impact of potential threats and enhancing the overall resilience of the Conflux network.
- Streamlined Integration and User Confidence: MetaScout aims to streamline its integration with the Conflux ecosystem, ensuring compatibility and functionality. By offering enhanced security and monitoring capabilities, MetaScout builds user confidence in the Conflux ecosystem. Users engaging in decentralized finance (DeFi) activities, particularly on Uniswap v4, can trust in the security provided by MetaScout, fostering a positive and secure environment.
 Objectives & Success Criteria of MetaScout on Conflux
Objectives & Success Criteria of MetaScout on Conflux
MetaScout aims to fortify the security landscape on the Conflux network through the implementation of advanced security features. By developing a robust monitoring infrastructure tailored for Conflux, the objective is to ensure real-time tracking and response mechanisms, fostering a secure and reliable environment for users engaged in decentralized finance activities. Seamless integration into the Conflux ecosystem is prioritized to provide Uniswap v4 users on Conflux with a user-friendly and efficient experience, ultimately empowering the Conflux community with a comprehensive security and monitoring toolset.
The success of MetaScout will be measured by a significant reduction in security incidents and vulnerabilities on the Conflux network, validating its effectiveness. Achieving a substantial adoption rate within the Conflux community, with users actively utilizing MetaScout for security and monitoring, will indicate positive integration metrics. The success will also be reflected in positive user feedback regarding the usability, effectiveness, and impact of MetaScout on their security needs. Moreover, demonstrating contributions to the overall Conflux ecosystem by fostering a secure environment and attracting more developers and users to Conflux will be key success indicators.
 Why choose MetaScout?
Why choose MetaScout?
MetaScout is uniquely positioned in the Conflux ecosystem as a comprehensive security platform, addressing critical gaps in existing monitoring tools, such as high error rates and inefficient asset recovery during fund theft incidents. Its advanced features, including mempool monitoring and migration attack detection, set it apart from other projects in the ecosystem and differentiate it from generic security solutions in the Conflux ecosystem. MetaScout’s tailored functionalities make it a distinctive and growth-focused security solution for Conflux.
TEAM
Our team is incubated by Nanyang Technological University in Singapore, with a strong troop of AI researchers and Web3 security researchers. We’re led by the co-founder Prof. Liu Yang, one of the outstanding Microsoft Asia Scholars. Security researchers and auditors in our team have experience in building security tools for developers in the web3 industry, and won trust from our clients like MAP Protocol, Uniwhale and Hope.money.
We’re focusing on risk mitigation and loss prevention at the research level and at the product level. Hope we can make the best of it with full effort.
- Prof. Yang Liu: Co-founder, professor at Nanyang Technological University in Singapore
https://www.linkedin.com/in/yang-liu-03a3a09/ - Mr. TY Shao: Partner of BD, 10 years experience in business development with 5 years experience in web3 investment
https://www.linkedin.com/in/tyshaosg/ - Ms. Angela Tong: COO, 10+ years in Crypto Marketing and Operation
- Mr. Simon Shieh: Head of Web3 Security Department, 7 years in Blockchain Development and Security
https://www.linkedin.com/in/simon-shieh-a2765a48/ - Mr. Andy Deng: Lead Engineer, 10+ Years in Software/Web Development & UI/UX
TOTAL BUDGET AND FUNDING TIER
Grant Tier: 3
Grant Size: $25k
Justification: The funds will be used for developement according the milestones.
Milestone 1
Budget Allocation: $2,000
Pre-launch Preparation (2023 Q2)
Milestone 2
Budget Allocation: $15,000
Product Launch (2023 Q3)
Milestone 3
Budget Allocation: $5,000
Migration Attack Engine and Contract Firewall (2023 Q4)
Milestone 4
Budget Allocation: $3,000
Optimization and Modular Enhancements (2024 Q1)
CURRENT FUNCTIONALITY
Customer Problems/Issues:
- Security Concerns: Users on Conflux may face security concerns due to potential vulnerabilities in the existing system, leading to risks such as unauthorized access, data breaches, and asset loss.
- Limited Monitoring: The current system may lack comprehensive monitoring features, leaving users without real-time insights into their transactions and potential security threats.
Application Problems/Issues:
- Vulnerability to Attacks: The current system may be susceptible to various attacks, including but not limited to smart contract exploits, unauthorized transactions, and manipulation of decentralized applications (DApps) running on Conflux.
- Inefficient Incident Response: Without an advanced security infrastructure, the system may struggle to efficiently respond to security incidents, leading to delays in addressing potential threats.
Processes Problems/Issues:
- Integration Challenges: Users may face challenges in integrating security tools seamlessly with the Conflux ecosystem, causing disruptions and compatibility issues.
- Lack of Proactive Measures: The absence of proactive security measures in the current system may result in a reactive approach to addressing security issues, impacting the overall resilience of the Conflux network.
What MetaScout can do:
Customer Solutions:
- Enhanced Security Features: MetaScout introduces advanced security features to address customer concerns, providing a more secure environment with reduced risks of unauthorized access and asset loss.
- Real-Time Monitoring: MetaScout’s robust monitoring infrastructure ensures customers have real-time insights into their transactions and activities, empowering them with proactive security measures.
Application Solutions:
- Mitigation of Security Vulnerabilities: MetaScout mitigates vulnerabilities by implementing proactive measures against smart contract exploits, unauthorized transactions, and potential attacks on DApps running on Conflux.
- Efficient Incident Response: The proposed system enhances incident response mechanisms, enabling swift identification and resolution of security incidents, reducing the impact on the Conflux network.
Processes Solutions:
- Seamless Integration: MetaScout is designed to seamlessly integrate with the Conflux ecosystem, addressing previous challenges and ensuring compatibility with existing processes.
- Proactive Security Measures: The new system introduces proactive security measures, deviating from a reactive approach and enhancing the overall resilience of the Conflux network by preventing security issues before they escalate.
MetaScout’s proposed functionality addresses the identified problems in the current system on Conflux, providing comprehensive solutions to enhance security, monitoring, and overall user confidence in the decentralized finance ecosystem.
TECHNICAL PROPOSAL
 Functional Requirements:
Functional Requirements:
- Security Features:
- Shall provide advanced threat detection: MetaScout shall include sophisticated algorithms to detect and respond to potential security threats, including smart contract exploits and unauthorized transactions.
- Real-Time Monitoring:
- Shall offer real-time transaction tracking: MetaScout shall provide users with a real-time view of their transactions on Conflux, ensuring immediate visibility into activities and potential security incidents.
- Incident Response:
- Shall facilitate swift incident response: MetaScout shall enable efficient identification and resolution of security incidents, minimizing the impact on the Conflux network.
- Seamless Integration:
- Shall integrate seamlessly with Conflux ecosystem: MetaScout shall be designed for seamless integration with the Conflux network, including compatibility with existing dApps and smart contracts.
- User-Friendly Interface:
- Shall feature a user-friendly interface: MetaScout shall provide an intuitive and easy-to-use interface for users to navigate and access security features without extensive technical expertise.
 Nonfunctional Requirements:
Nonfunctional Requirements:
-
Usability:
- Shall ensure user accessibility: MetaScout shall prioritize an accessible user interface, ensuring that security features are easily understandable and navigable for users of varying technical backgrounds.
-
Reliability:
- Shall maintain high reliability: MetaScout shall operate with high reliability, minimizing downtime and ensuring consistent availability to Conflux users.
-
Performance:
- Shall exhibit optimal performance: MetaScout shall be designed for optimal performance, ensuring minimal latency in real-time monitoring and rapid response to security incidents.
-
Supportability:
- Shall provide adequate support documentation: MetaScout shall include comprehensive documentation to assist users in understanding and utilizing the system effectively, including troubleshooting and best practices.
-
Implementation:
- Shall adhere to best coding practices: MetaScout’s implementation shall adhere to industry best coding practices, emphasizing code quality, modularity, and maintainability.
-
Interface:
- Shall offer a general set for integration: MetaScout shall provide a general interface to facilitate integration with other tools and systems within the Conflux ecosystem.
-
Packaging:
- Shall provide easy subscription and updates: MetaScout shall have a user-friendly packaging approach, ensuring straightforward subscription processes and seamless updates to new versions.
SYSTEM MODEL
MetaScout is still in alpha stage.
ECOSYSTEM FIT
- Enhanced Security Infrastructure: By providing advanced security features and real-time monitoring, MetaScout strengthens the security infrastructure of the Conflux network. This enhanced security creates a more trustworthy environment for developers, users, and decentralized applications dApps, fostering confidence in the ecosystem.
- Attraction of Developers: MetaScout’s integration seamlessly with the Conflux ecosystem and its focus on security addresses critical concerns for developers. The availability of a reliable security tool encourages more developers to build and deploy their applications on Conflux, expanding the ecosystem with innovative decentralized solutions.
- Positive User Experience: The user-friendly interface and proactive security measures offered by MetaScout enhance the overall user experience on Conflux. This positive experience encourages user retention and attracts new participants, leading to a more engaged and growing user base.
DEVELOPMENT ROADMAP
 Milestone1
Milestone1
Pre-launch Preparation (2023 Q2)
- Deliverables:
- Finalization of product development roadmap.
- Completion of internal testing and quality assurance procedures.
- Establishment of communication channels for user feedback.
- Implementation of initial marketing strategies.
- KPI Goals:
- Successful completion of internal testing with no critical issues.
- Feedback collection from an internal testing team.
- Creation of initial brand awareness through pre-launch marketing efforts.
- Expected Date of Achievement: 2023 Q2.
 Milestone 2
Milestone 2
Product Launch (2023 Q3)
- Deliverables: MetaScout product officially launched.
- KPI Goals: Successful deployment and positive user feedback on the MetaScout platform.
- Expected Date of Achievement: 2023 Q3.
 Milestone 3
Milestone 3
Migration Attack Engine and Contract Firewall (2023 Q4)
- Migration Attack Engine Development
- Bytecode similarity engine
- Source code function similarity engine
- Source code snippet similarity engine
- KPI Goals: Reduction in migration attack false positives by 30%.
- Contract Firewall Development
- Proxy firewall contract
- Forwarder callback contract
- ERC4771 Lib contract
- Off-chain analysis system
- Off-chain callback system
- KPI Goals: Achieve a 20% increase in on-chain security effectiveness
- Early-Response System Development
- Mempool attack detection system
- Flash-block node optimization
- KPI Goals: Reduce response time to mempool attacks by 40%
- Expected Date of Achievement: 2023 Q4
 Milestone 4
Milestone 4
Optimization and Modular Enhancements (2024 Q1)
- Flash-Block Node Optimization
- Enhancements to the Flash-block node for improved performance
- KPI Goals: Achieve a 25% improvement in Flash-block node efficiency
- Increased Private and Modular Capabilities
- Capability for private deployment
- Modular deployment for enhanced flexibility
- KPI Goals: Enable private deployment for 10% of MetaScout users; achieve a 15% increase in user satisfaction with modular features
- Intellectual Property Development
- 3 patent submissions
- Contract firewall
- Early-stop mechanism
- Monitoring of malicious contract deployments
- KPI Goals: Successfully file patents; receive positive reviews from the blockchain community
- EIP Submission
- Ethereum Improvement Proposal for the contract firewall
- KPI Goals: Obtain community support for the EIP; contribute to the Ethereum protocol’s enhancement
- Expected Date of Achievement: 2024 Q1.
 Additional Developments (2024 Q2~Q4)
Additional Developments (2024 Q2~Q4)
KPI Goals: Successfully integrate MetaScout with 20 web3 protocols; achieve a 30% increase in user engagement across integrated protocols.
MAINTENANCE CONSIDERATIONS
- Continuous Improvement and User Engagement:
- MetaScout will prioritize regular updates and feature enhancements to meet evolving user needs in the dynamic blockchain monitoring space. Community engagement through webinars, Q&A sessions, and forums will foster an active user community, ensuring MetaScout remains user-friendly and aligned with user expectations.
- Robust Security Measures and Data Protection:
- While MetaScout primarily focuses on monitoring, ensuring the security and privacy of user data is paramount. The post-grant plan includes implementing and regularly updating robust security measures to safeguard user information. This commitment to data protection reinforces user trust in MetaScout’s reliability.
- Scalability, Compatibility, and Collaboration:
- MetaScout’s post-grant strategy includes evaluating and optimizing system scalability to accommodate the growing Conflux ecosystem. Ensuring compatibility with new blockchain developments will be a priority, facilitated by ongoing collaboration with Conflux developers. Active participation in community discussions and contribution to the ecosystem’s growth will solidify MetaScout’s position as a valuable asset within Conflux.